iShredder

Thank you for
downloading iShredder Android
One last step...
Enter your email address to receive your download link and
installation instruction by email.
Top reasons to
Choose iShredder
Irreversible Deletion
Prevent sensitive data from being recovered later. iShredder™ removes files so thoroughly that even professional recovery tools fail.
Certified Deletion Algorithms
Whether it’s DoD 522.22-M, NIST SP 800-88, BSI TL-03423, or other recognized standards—iShredder™ uses algorithms trusted by the military and government agencies alike.
Three Steps to Success
Simply select the data you want to erase, choose the deletion algorithm, and confirm with one click. Your data is securely gone.
Cleaning Temporary Files
iShredder™ also hunts down hidden caches, logs, and other leftovers. This frees up storage space and prevents unwanted data traces.
Perfect for Selling Your Device
No one should gain access to your private photos, passwords, or other information. With iShredder™, you can safely pass on your smartphone, tablet, or PC.
Deletion Reports & Documentation
For extra assurance, iShredder™ generates a detailed report for each deletion action—ideal for businesses that need GDPR-compliant records.
Military-grade
secure deletion
iShredder™ is the most popular data shredder for iOS, Android, Windows, and Mac. The app is equally suitable for beginners and professionals to delete data securely. Deletion report included.
iShredder™ deletes so securely with international military security standards that defense departments and government agencies use the technology.
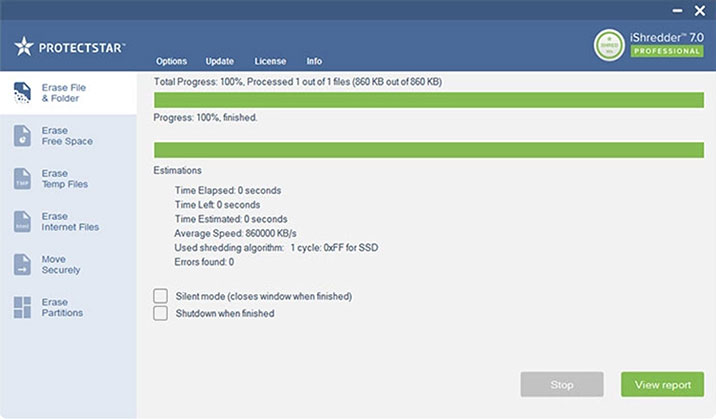
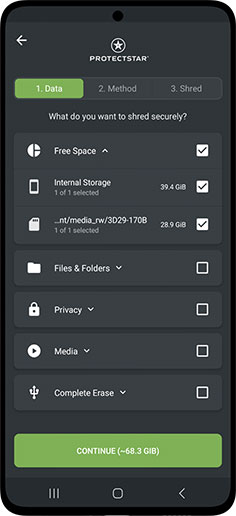
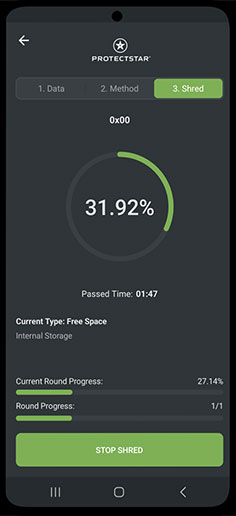
Irreversible Deletion in Three Steps
For example, suppose you have deleted files such as documents or photos. In that case, this manually deleted data can be recovered from the device's free space until the data has been securely overwritten using deletion algorithms.
In just three steps, your files or storage space will be overwritten according to patented security standards, and data recovery will be impossible:
Select the data you want to delete
Choose between 20 and more deletion methods

Begin to shred with one simple click
Deleted Doesn’t Necessarily Mean Gone
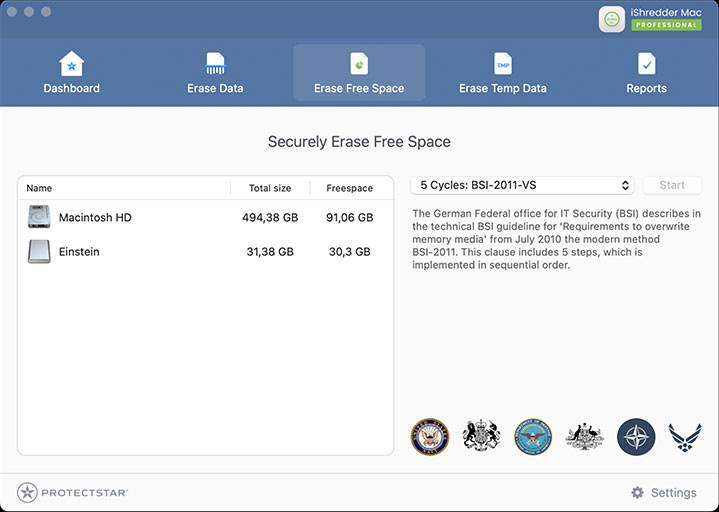
Even after so-called “deletion” or “formatting,” a large portion of your files can still be recovered. iShredder™ shows you exactly what remnants lurk in free space and uses powerful routines to keep anyone from reconstructing those fragments.
Use the “Securely Erase Free Space” feature in iShredder™ to securely overwrite free space so that previously deleted data cannot be recovered.
Certified Security
iShredder™ Android is officially DEKRA MASA L1 certified, meeting rigorous OWASP standards for data protection and mobile app security. Permanently erase sensitive data with confidence, using an app independently verified to be free of vulnerabilities.

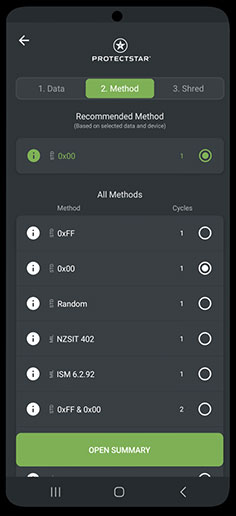
Certified deletion algorithms
With over 20 approved erasure algorithms, iShredder™ even exceeds international government and military security standards for secure data erasure. In addition, authorities and independent organizations have analyzed each deletion method for its security and to ensure safe data destruction.
Depending on the edition used, erasure algorithms such as DoD 5220.22-M E, U.S. Air Force (AFSSI-5020), U.S. Army AR380-19, DoD 5220.22-M ECE, BSI/VS-ITR TL-03423 Standard, BSI-2011-VS, BSI TL-03423, NATO Standard, CSEC ITSG-06, HMG InfoSec No.5, DoD 5220.22 SSD and others are available.
Specifically developed by Protectstar™ Inc. in 2007 it runs through fifty erasure routines.
Data will be overwritten for two times with a random value, afterwards with their complements. It includes and the DoD 5220.22-M (E) standard and Peter Gutmann method and random algorithms.
The algorithm from Peter Gutmann was found in 1996 and makes 35 overwrite passes in total.
This algorithm is one of the state-of-the-art methods for data destruction.
In March 2010 the German Federal office for IT Security (BSI) published a new technical BSI Guideline for "Requirements to overwrite memory media".
The method is similar to VSITR standard for magnetic storage media.
In total the new algorithm has 8 cycles, which has to be worked through in chronological order. Includes one cycle of verification.
The NATO method is the deletion standard of North Atlantic Treaty Organization (NATO).
It will overwrite the target data area 7 times.
The first six overwrites are with the fixed values (0x00) and (0xff), alternating between passes.
The 7th overwrite is with a random value i.e. 0x00,0xFF,0x00,0xFF,0x00,0xFF and 7th pass with a random value.
The method for high security is based on the January 1995 'National Industrial Security Program Operating Manual'by the Department of Defense (DoD).
In this seven cycle variation (DoD 5220.22-M ECE), data is first overwritten three times with DoD 5220.22-M (E) Standards, then with a specific random value, and finally once again with DoD 5220.22-M (E).
The Royal Canadian Mounted Police Standard RCMP TSSIT OPS-II overwrites data securely with alternating sequences with a total of seven cycles.
The German Federal office for IT Security (BSI) describes in the technical BSI guideline for 'Requirements to overwrite memory media' from July 2010 the modern method BSI-2011.
This clause includes 5 steps, which is implemented in sequential order.
This method is specially developed for SSD (Solid State Drive) and flash memory, based on the U.S.
Department of Defense's standard DoD 5220.22-M E. It will overwrite data four times.
This method is specially developed for SSD (Solid State Drive) and flash memory, based on the U.S.
Department of Defense's standard DoD 5220.22-M E. It will overwrite data four times.
The Canadian CSEC ITSG-06 sanitization method has three cycles and was published in 2006 by Communication Security Establishment Canada (CSEC).
The HMG Infosec Standard No 5 - enhanced level is approved to wipe UK Government Top Secret data and has also been approved by NATO.
The algorithm is a three pass overwriting algorithm: first pass - with zeros (0), second and third passes with its compliment and random values(with last pass verification).
The AFSSI-5020 sanitization method was originally defined in the Air Force System Security Instruction 5020 by the United States Air Force (USAF) in 1996 and may still be today.
This is the US Navy standard NAVSO P-5239-26 for MFM encoded drives.
This deletion method first writes the fixed value (0xffffffff) to the target data area, then the fixed value (0xbfffffff) and then random values.
Finally, the target data area is read to verify the overwrites.
This is the US Navy standard NAVSO P-5239-26 for RLL encoded drives.
This deletion method first writes the fixed value (0xffffffff) to the target data area, then the fixed value (0x27ffffff) and then random values.
Finally, the target data area is read to verify the overwrites.
AR380-19 is the data shredding algorithm specified and published by the U.S. Army.
The algorithm is a three pass overwriting algorithm: first pass - with random bytes, second and third passes with certain bytes and with its compliment (with last pass verification).
The method for low security but for high execution speed is based on the January 1995 'National Industry Security Program Operating Manual' from the DoD (US DoD 5220.22-M).
The variation (DoD 5220.22-M E) offers 3 cycles in which the data are overwritten with first a set value, then its compliment, and then a random value.
The American NCSC-TG-025 standard of the National Computer Security Center (NCSC) securely overwrites existing information on a data medium three times.
The in 2006 released standard is the Special Publication 800-88 from NIST, which is the go-to data erasure standard for organizations in the United States. Its principles can apply to magnetic, flash-based, and other storage technologies, from USB drives to servers.
The Russian data deletion standard GOST R 50739-95 for secure data erasure overwrites the target data are two tome. In the first pass with a zero, and in the second pass with random characters.
ISM 6.2.92 is the Australian government's data sanitization standard.
The method was originally defined in the Information Security Manual (ISM) issued by the Australian Department of Defense: Intelligence & Security.
The ISM 6.2.92 sanitization can not be used to sanitize classified information.
This method is specially developed for SSD (Solid State Drive) and flash memory.
It offers one cycle which data are overwritten by the pattern "0xFF".
This method for lowest security but for very high execution on speed. It offers only one cycle which data are overwritten with random values.
In December 2014, the guidelines were revised, making the current version “NIST Special Publication 800-88 Rev. 1”.
See here the description of the method you have selected.
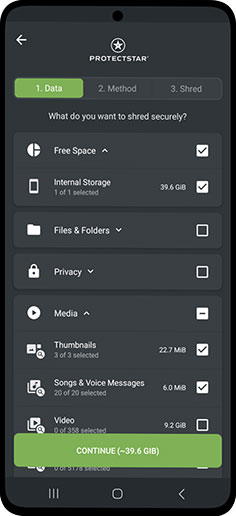
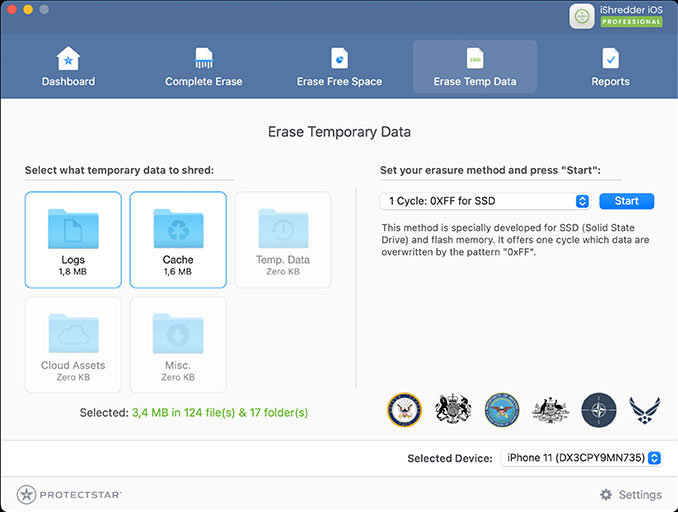
Cleaning Up Temporary Data
What many people overlook are browser caches, log files, and other temporary storage. iShredder™ cleans these areas as well, giving you more free storage and protecting your privacy.
You Want to Sell Your Device
Unknown security risk? No thanks!
Whenever you resell a smartphone, laptop, or tablet, there’s usually still a digital footprint of your personal data left behind. iShredder™ irreversibly deletes those traces, ensuring no stranger can access photos, passwords, or documents. That means you can hand over or sell your device with total peace of mind.
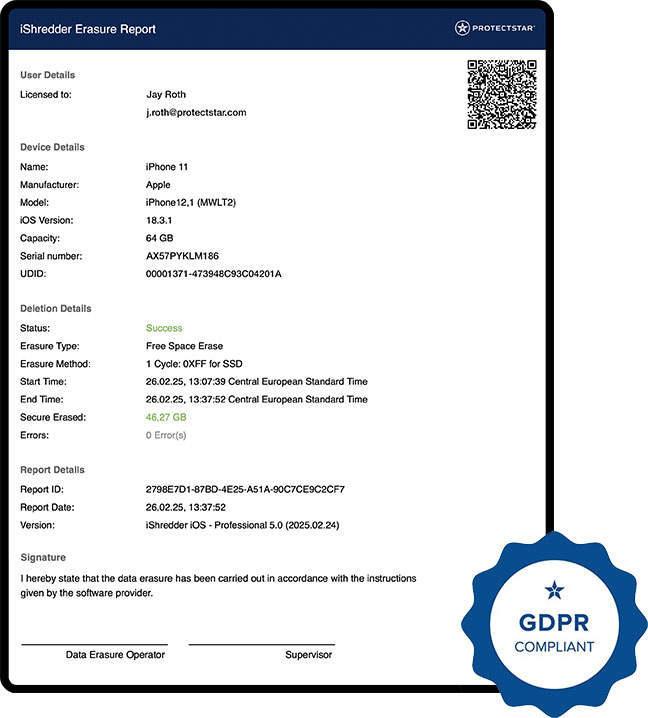
100% Confidence: Detailed Deletion Reports
After every deletion action, iShredder™ creates a comprehensive report with a timestamp, file list, and the algorithm used. This is your proof that the data truly is gone—ideal for businesses needing GDPR compliance (or UK Government InfoSec No. 5, U.S. DoD, NIST 800-88) or for private users who insist on top-notch security.
What people say about us

4M+
Downloads
Trust iShredder™—the #1
in Secure Data Erasure.
Download iShredder™ for free now, or choose the edition (Free, Pro, Military, GOV) that best meets your needs.
Enjoy military-grade erasure protection without complicated settings.




-
Securely overwrite the freespace
-
Secure freespace wipe of SD card
-
Preinstalled standard deletion algorithms
-
Wipe methods in total: 4
-
Create and Export Erasure Reports
-
Securely overwrite the freespace
-
Secure freespace wipe of SD card
-
Preinstalled standard deletion algorithms
-
Wipe methods in total: 14
-
Securely wipe SD card
-
Secure delete external usb sticks, hard disk, etc.
-
Securely Erase files and folders
-
Securely Erase media files
-
Securely Erase contacs and clipboard
-
Create and Export Erasure Reports
MILITARY
Best for users who want the military-grade features
-
Securely overwrite the freespace
-
Secure freespace wipe of SD card
-
Preinstalled standard deletion algorithms
-
Wipe methods in total: 25
-
Securely wipe SD card
-
Secure delete external usb sticks, hard disk, etc.
-
Securely Erase files and folders
-
Securely Erase media files
-
Securely Erase contacs and clipboard
-
Additional Military Grade and Enterprise deletion methods
-
Set default deletion method
-
Password Protection
-
Create and Export Erasure Reports
-
Securely overwrite the freespace
-
Secure freespace wipe of SD card
-
Preinstalled standard deletion algorithms
-
Wipe methods in total: 25
-
Securely wipe SD card
-
Secure delete external usb sticks, hard disk, etc.
-
Securely Erase files and folders
-
Securely Erase media files
-
Securely Erase contacs and clipboard
-
Securely Erase SMS, MMS and call logs
-
Additional Military Grade and Enterprise deletion methods
-
Set default deletion method
-
Password Protection
-
Create and Export Erasure Reports
PRO
Best for users who want to have more advanced features
-
Secure erase of files, folders and partitions
-
Secure cutting and pasting of files and directories
-
Secure erase of external devices
-
Smart secure erase wizard
-
Secure erase of temporary Windows files
-
Secure erase of temporary internet files
-
Advanced deletion logs
-
Special secure wiping algorithms for SSD & flash memory
-
Protectstar™ Secure Deletion Algorithm
-
Data Shredder for Solid State Drives
-
1 Year technical support
-
11 erasing methods in total
MILITARY
Best for users who want the military-grade features
-
Secure erase of files, folders and partitions
-
Secure cutting and pasting of files and directories
-
Secure erase of external devices
-
Smart secure erase wizard
-
Secure erase of temporary Windows files
-
Secure erase of temporary internet files
-
Advanced deletion logs
-
Special secure wiping algorithms for SSD & flash memory
-
Protectstar™ Secure Deletion Algorithm
-
Data Shredder for Solid State Drives
-
Enhanced military deletion methods like NATO standard, US Navy NAVSO P-5239-26 , USAF AFSSI-5020 and CSEC ITSG-06.
-
1 Year technical support
-
18 erasing methods in total
PRO
Best for users who want to have more advanced features
-
Compatible with all models of MacBook, MacBook Air, Macbook Pro, iMac, iMac Pro and Mac Pro
-
Secure data deletion up to the top secret security standard level
-
Deletion algorithms like DoD 5220.22-M ECE, Peter Gutmann, DoD 5220.22-M, HMG Infosec No.5, German BSI-2011-VS, US Army AR380-19 and more
-
Detailed erasure report provides evidence of deletion
-
Compatible with Solid State Drives (SSD) and Flash memory
-
Full Drag & Drop support
-
Erasing methods in total (11)
-
Incl. 1 year technical support and free upgrades
-
24/7 Support by e-Mail
MILITARY
Best for users who want the military-grade features
-
Compatible with all models of MacBook, MacBook Air, Macbook Pro, iMac, iMac Pro and Mac Pro
-
Secure data deletion up to the top secret security standard level
-
Deletion algorithms like DoD 5220.22-M ECE, Peter Gutmann, DoD 5220.22-M, HMG Infosec No.5, German BSI-2011-VS, US Army AR380-19 and more
-
Detailed erasure report provides evidence of deletion
-
Compatible with Solid State Drives (SSD) and Flash memory
-
Full Drag & Drop support
-
Advanced deletion reports
-
Enhanced military deletion methods like NATO standard, US Navy NAVSO P-5239-26 (MFM & RLL), USAF AFSSI-5020, BSI TL-03423 and CSEC ITSG-06
-
Erasing methods in total (21)
-
Incl. 1 year technical support and free upgrades
-
24/7 Support by e-Mail
PRO
Best for users who want to have more advanced features
-
Compatible with all iPhone®, iPad® and iPod® touch models
-
Compatible with all iOS® versions
-
Securely overwrite the freespace
-
Complete wipe of all data on the iOS® device
-
Secure cleaning of temporary data
-
Incl. 1 year technical support and free upgrades
-
Advanced deletion reports
-
24/7 Support by e-Mail
-
11 erasing methods in total
-
Protectstar™ Advanced Secure Deletion Algorithm (2017)
MILITARY
Best for users who want the military-grade features
-
Compatible with all iPhone®, iPad® and iPod® touch models
-
Compatible with all iOS® versions
-
Securely overwrite the freespace
-
Complete wipe of all data on the iOS® device
-
Secure cleaning of temporary data
-
Incl. 1 year technical support and free upgrades
-
Advanced deletion reports
-
Integrated Secure File Explorer
-
Securely delete AppleTV (all models)
-
24/7 Support by e-Mail
-
18 erasing methods in total
-
Protectstar™ Advanced Secure Deletion Algorithm (2017)
-
50-cycles wiping method Protectstar™ Secure Deletion Algorithm®




